 |
Intuitively, we would like
to let fan(x) (n is a sufficiently large integer) be the
ciphertext corresponding to a plaintext
![]() .
However,
decryption uniqueness would be lost in this configuration since fais two-to-one. To overcome this improperness, we discretize the plaintext
space, the ciphertext space, the key space, and the transformation,
constructing a one-to-one map explicitly.
.
However,
decryption uniqueness would be lost in this configuration since fais two-to-one. To overcome this improperness, we discretize the plaintext
space, the ciphertext space, the key space, and the transformation,
constructing a one-to-one map explicitly.
For simplicity, we stretch the domain and the range of the skew tent
map from [0,1] to [0,M]. We denote this rescaled skew tent map by
FA. The integer
M = 2128 is equal to the cardinality of the
plaintext space
![]() ,
the ciphertext space
,
the ciphertext space
![]() ,
and
the key space
,
and
the key space
![]() ;
these spaces are defined by
;
these spaces are defined by
Next, let us consider the conditions for a discretized skew tent map
to satisfy
(see Fig. 2). The black points on the x axis is the points
in
![]() .
If we set FA(X) as the state after
transforming
.
If we set FA(X) as the state after
transforming
![]() ,
there would arise two inconsistencies:
a point from the left and another
point from the right would possibly collide after transformation, and
generally speaking,
,
there would arise two inconsistencies:
a point from the left and another
point from the right would possibly collide after transformation, and
generally speaking,
![]() .
Accordingly, we define a discretized skew tent map
.
Accordingly, we define a discretized skew tent map
![]() as follows:
as follows:
X is transformed into the number of black points in the region enclosed with the two circles in Fig. 2.
If
FA(X1) = FA(X2), X1 < A < X2, then we define
![]() and
and
![]() so that
so that
![]() .
.
![]() is one-to-one mapping on
is one-to-one mapping on
![]() .
.
FS-CES is defined by the encryptor
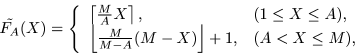
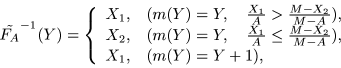
 |